Last Updated on 19/01/2026 by Damin Murdock
For Australian businesses developing software or designing algorithms, whether for internal use or commercial ventures, understanding the fundamental layers of intellectual property protection is crucial. While basic software copyright often arises automatically upon creation under Australian copyright law, a proactive approach to IP protection should be taken to prevent misuse and to improve your enforcement capabilities.
This legal guide goes beyond the basic principles of software copyright Australia, exploring the specific protections available for algorithms and detailed strategies for broader IP protection in Australia.
How Australian Law Protects Software and Algorithms
Under the Copyright Act 1968 (Cth), software’s underlying code, including both the human-readable source code and the machine-readable object code, is specifically protected as a “literary work.” This fundamental classification grants creators automatic copyright rights from the moment the code is written, forming the foundation of software protection in Australia.
The High Court affirmed the core protection of computer programs in Computer Edge Pty Ltd v Apple Computer Inc [1986] HCA 19. Further, cases like Microsoft Corp v Business Boost Pty Ltd [1999] FCA 1384 clarified that copyright extends to any original “expression of instructions” designed to make a device perform a specific function, irrespective of the programming language or format used. This broad interpretation is particularly relevant for diverse software components and algorithms, which embody such instructions.
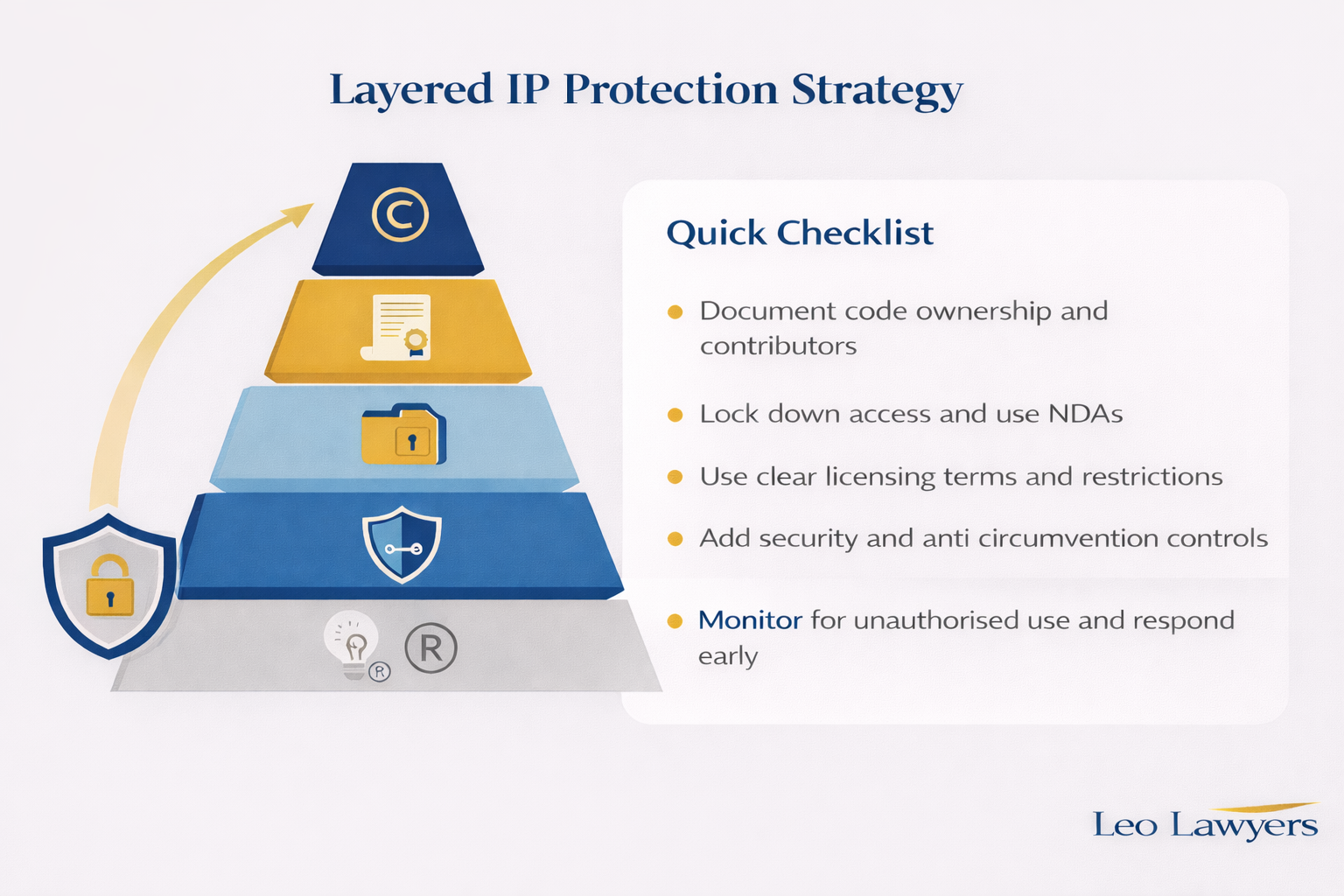
Proactive IP Management: Beyond Automatic Protection
While software copyright exists automatically, proactive steps are necessary to protect the copyright that includes careful documentation, strategic use of technical safeguards such as imbedded anti-piracy code or software, and carefully constructed software legal agreements.
- Careful Documentation & Proof of Originality:
Businesses should maintain detailed records that clearly establish every contributor to the original source code, along with precise creation dates, a clear development timeline, and comprehensive logs of all versions, updates, and changes. It is also vital to pinpoint and document which specific parts of your software and algorithms are original, as this qualifies them for copyright protection. This level of detail proved instrumental in cases like Campaigntrack Pty Ltd v Real Estate Tool Box Pty Ltd [2021] FCA 809, where clear proof of authorship and originality was key to enforcing software copyright.
- Strategic Technical Safeguards & Anti-Circumvention:
Beyond basic access controls, Australian businesses should implement advanced technical barriers to prevent unauthorised copying, use, or reverse engineering of their software assets. This includes utilising robust version control systems, comprehensive license management tools, and anti-circumvention measures to prevent users from bypassing software protection technologies. For instance, you can have a look at Cylynt (formerly SmartFlow), Hyperproof, Laika, CloudLock, Flexera Software, AppGuard, CodeMeter, SafeNet Sentinel, Arxan, Denuvo, and Pretectus. The legal protection afforded to these technical measures is supported by High Court decisions, such as Stevens v Sony Computer Entertainment [2005] HCA 58, which acknowledge the importance of technological locks for digital asset protection whereby Sony had a key-lock technological protection measure, and Steven used a modchip to circumvent that protection measure.
- Comprehensive Legal Notices and Tailored Licenses:
Your software legal agreements are a cornerstone of effective IP management. Businesses should integrate clear copyright notices directly into their source code, object code, and user interfaces. It is also crucial to utilise properly structured software license agreements (EULAs) that explicitly define ownership of the software and its components, general permissions and restrictions, and specific prohibitions like reverse engineering, decompiling, or redistribution. Often times companies enter into enterprise agreements with its customers, but have no EULA for the actual users, who are normally the customer’s employees and contractors. This additional step should not be forgotten. Understanding and ensuring compliance with your licence is important to be able to enforce your legal. This approach to software licensing and dependencies is increasingly important, as highlighted in cases like Siemens Industry Software Inc v Telstra Corp Ltd [2020] FCA 901, where Siemens was able to use preliminary discovery procedures in the Federal Court to identify potential copyright infringers.
This image and its contents are protected by copyright under Australian law and international treaties. Leo Lawyers Pty Limited reserves those rights.
Enforcing Your Rights: Beyond Damages
If your software or algorithms is used without authorisation, Australian law provides sufficient reliefs. Beyond financial compensation for losses or profits made from infringement, courts can award additional damages in cases of flagrant or deliberate misuse, or where someone has circumvented your technological protection measure.
In addition to damages, you may also seek injunctive relief, a powerful legal order compelling the infringing party to immediately cease using or distributing your software. The comprehensive scope of legal remedies available for software infringement was successfully pursued in Motorola Solutions, Inc. v Hytera Communications Corporation Ltd (Liability) [2022] FCA 1585 where Hytera was using Motorola’s firmware code, and authorising dealers to make copies of the firmware code.
Important Things to Keep in Mind for Comprehensive IP Protection
While software copyright is foundational, a truly robust IP protection strategy for software and algorithms extends beyond it:
- Copyright Has Limits: copyright protects how an idea is expressed, not the underlying idea, functionality, or algorithm itself. If someone independently creates software performing a similar function without copying your code, they may not be infringing. This distinction highlights the need for other protections like patents for software or trade secrets for algorithms.
- Proactive Monitoring and Auditing: Regular auditing your intellectual property assets and customers to ensure compliance and identify vulnerabilities is an important measure. This should also include monitoring the market for similar or potentially copied software, and maintain legal records of your code’s creation and evolution.
- Complementary Protections: You should not solely rely on copyright. Implementing a layered approach to software protection should also be considered, for instance:
- Confidentiality agreements (NDAs) for staff, contractors, and partners handling sensitive software code.
- Terms of use for customers to define acceptable usage of your digital products.
- Trade secret protections for algorithms, proprietary code logic, or unique development processes that give you a competitive edge and are actively kept secret (a key aspect of algorithm protection).
- Consider International Protection: If your software or algorithms are used globally, be mindful that copyright laws vary by jurisdiction. While international agreements like the Berne Convention offer baseline protections, a comprehensive global strategy may involve understanding and securing rights in specific target countries for full international IP protection.
Final Thoughts
Software and algorithm development represents a significant, often intangible, business asset that demands sophisticated legal protection. While Australian copyright law offers strong foundational safeguards, your ability to enforce those rights and maximise their commercial value depends heavily on how thoroughly you document, license, and proactively manage all aspects of your digital intellectual property.
At Leo Lawyers, we empower Australian businesses, developers, founders, and business leaders to protect their complex digital products with tailored legal solutions. Feel free to contact Damin Murdock at Leo Lawyers via our website, on (02) 8201 0051 or at office@leolawyers.com.au. Further, if you liked this article, please subscribe to newsletter via our Website, and subscribe to our YouTube , LinkedIn, Facebook and Instagram. If you liked this article or video, please also give us a favourable Google Review.
DISCLAIMER: This is not legal advice and is general information only. You should not rely upon the information contained in this article and if you require specific legal advice, please contact us
Damin Murdock (J.D | LL.M | BACS - Finance) is a seasoned commercial lawyer with over 17 years of experience, recognised as a trusted legal advisor and courtroom advocate who has built a formidable reputation for delivering strategic legal solutions across corporate, commercial, construction, and technology law. He has held senior leadership positions, including director of a national Australian law firm, principal lawyer of MurdockCheng Legal Practice, and Chief Legal Officer of Lawpath, Australia's largest legal technology platform. Throughout his career, Damin has personally advised more than 2,000 startups and SMEs, earning over 300 five-star reviews from satisfied clients who value his clear communication, commercial pragmatism, and in-depth legal knowledge. As an established legal thought leader, he has hosted over 100 webinars and legal videos that have attracted tens of thousands of views, reinforcing his trusted authority in both legal and business communities."


